DevOps evolution in 2019: IT Svit perspective
-
3540
-
5
-
10
-
0
DevOps as an approach to cloud infrastructure management and optimization of IT operations is a decade old, as the term was coined in 2009. Throughout this decade DevOps became the mainstream approach to software delivery and it does not stop evolving. IT Svit compares our DevOps journey experience of 2019 with the findings of the Puppet State of DevOps report 2019. Read to learn why security is paramount for DevOps culture in 2019.
Back in 2017, Forrester predicted 2018 to be the year of corporate DevOps, as 50%+ of enterprises worldwide were already actively implementing DevOps initiatives in their workflows. DORA & Puppet’s report on the State of DevOps adoption in 2017 highlighted the fact that most of the businesses went to cloud platforms like AWS, Google Cloud or Azure and started learning to use cloud-native tools like Google Kubernetes Engine or Amazon CloudTrail.
In 2018, Puppet reported that the major DevOps implementation was going along nicely, but the majority of companies stalled in their progress. The experts continued to analyze the situation and offered a 5-step roadmap to DevOps implementation that was taken by the top-performers and has lead to the most significant results. We have showcased how IT Svit applies these practices and roadmaps to successfully deliver value and accomplish projects for our customers.
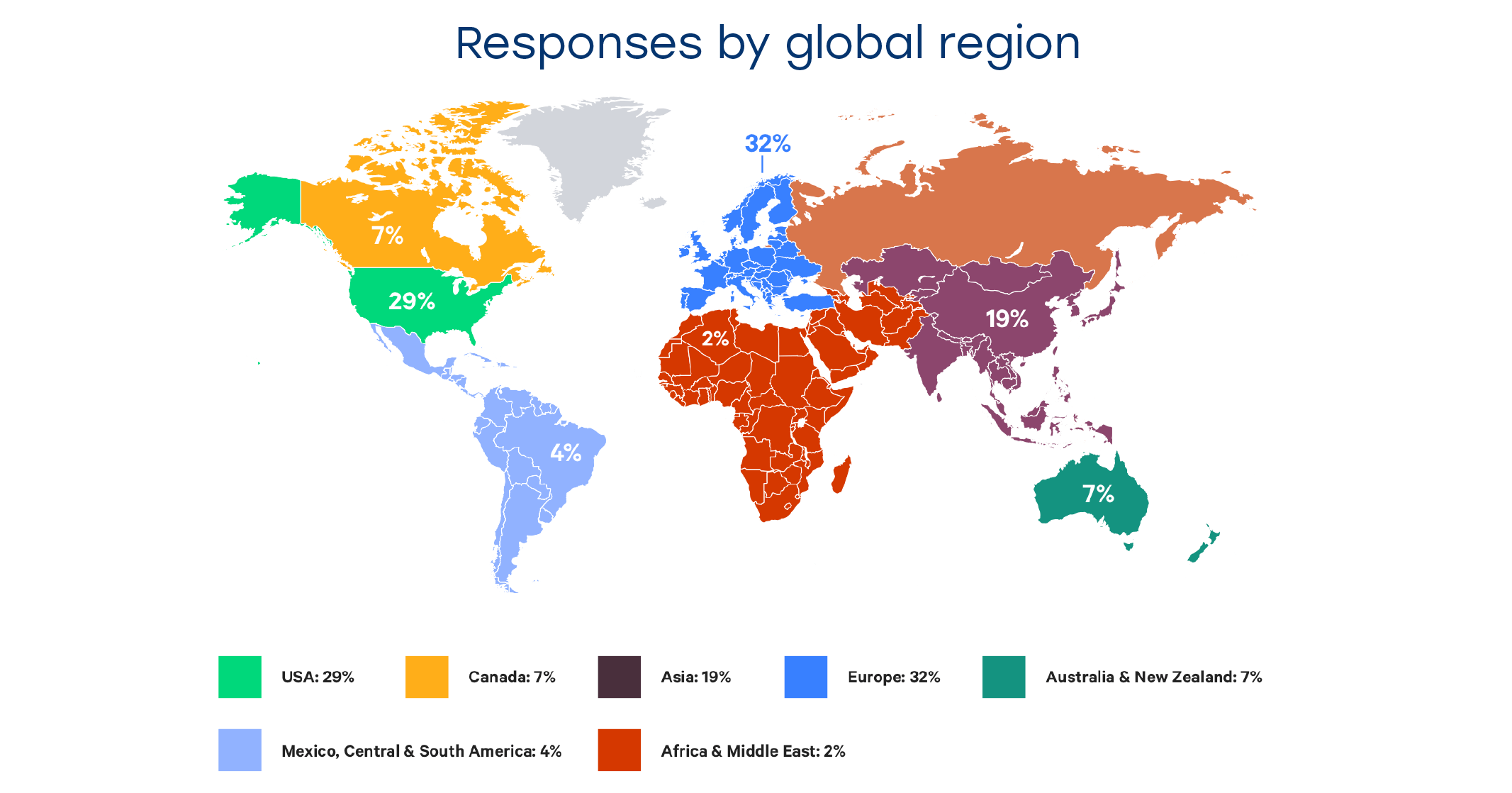
Fast-forward to 2019 and the annual Puppet report of the State of DevOps in 2019 is out. It continues to analyze the progress of the industry-wide DevOps adoption and highlights the main issue most of the companies stumble upon — cybersecurity. We have read this report and prepared a brief summary of 86 pages filled with input from about 3,000 C-level executives, DevOps professionals and technology experts, who took part in this 8th annual survey.
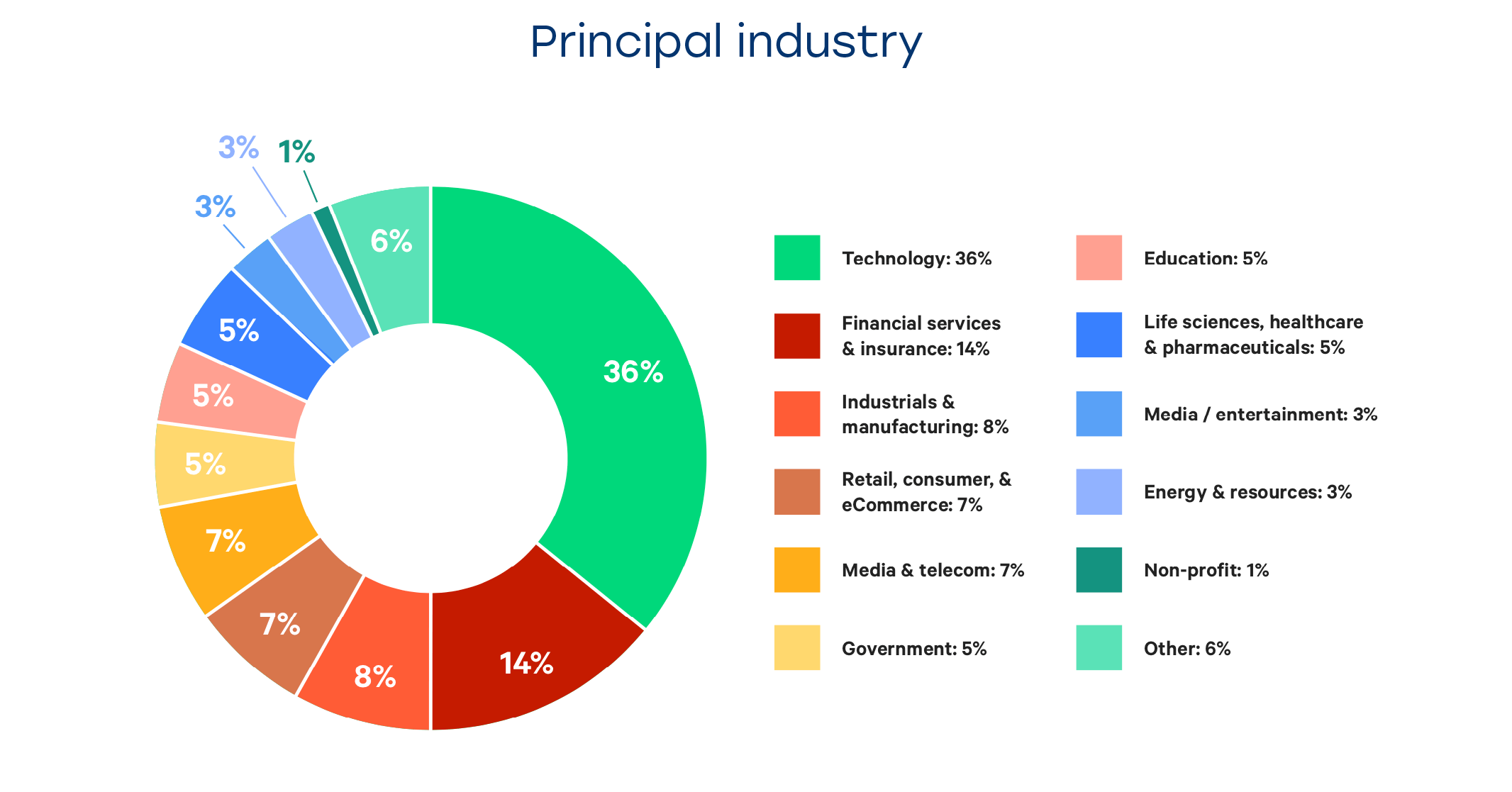
Continue reading to get a brief excerpt on the best practices of cybersecurity implementation in 2019, as well as a showcase of IT Svit approach to cybersecurity, and several of our case studies.
DevOps in 2019: design with cybersecurity in mind
As we mentioned before, Puppet has compressed the responses from nearly 3,000 respondents into 86 pages of text. We provide the excerpts of that, giving you the ability to make informed business decisions based on the findings of industry-leading experts.
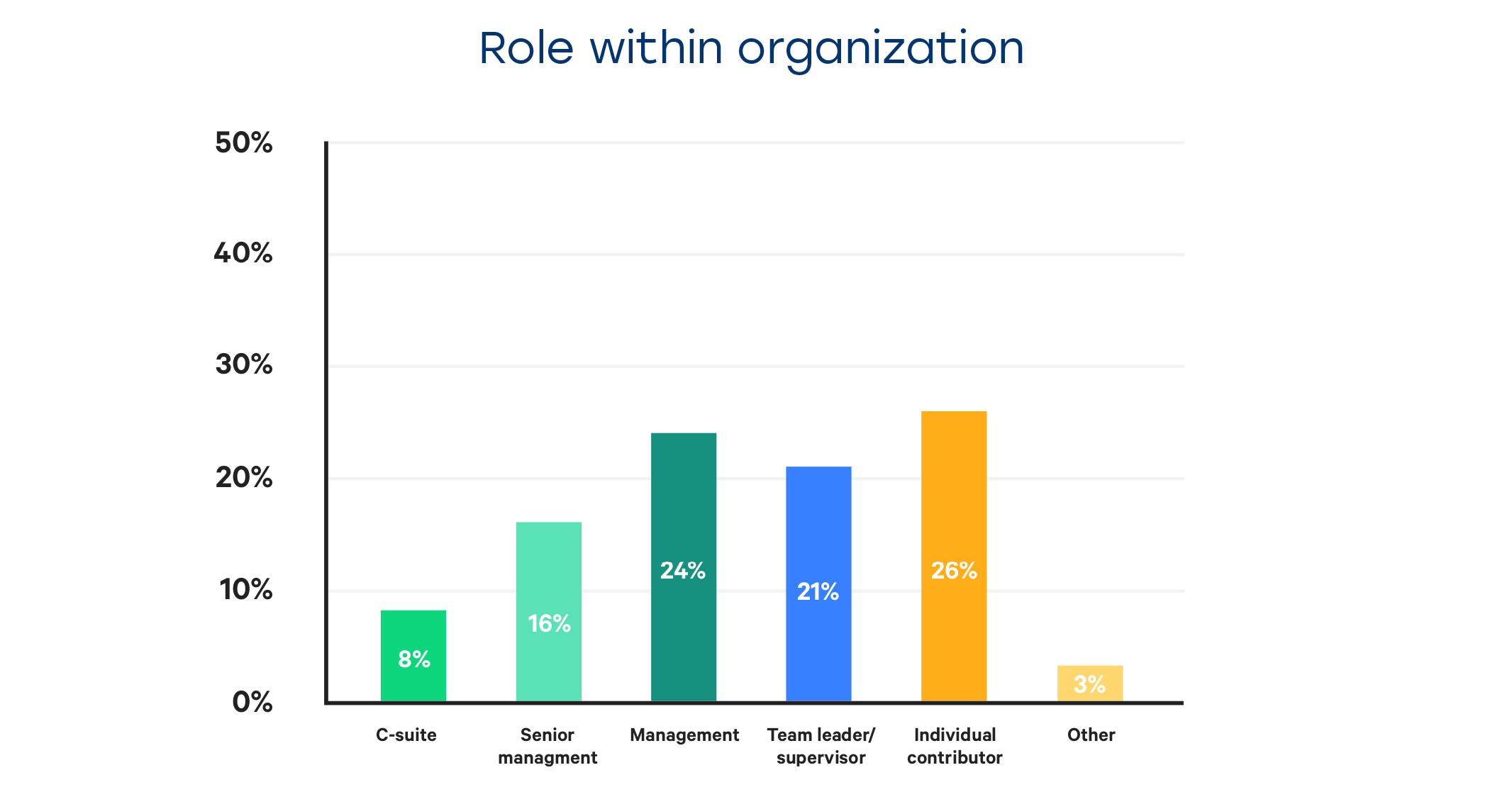
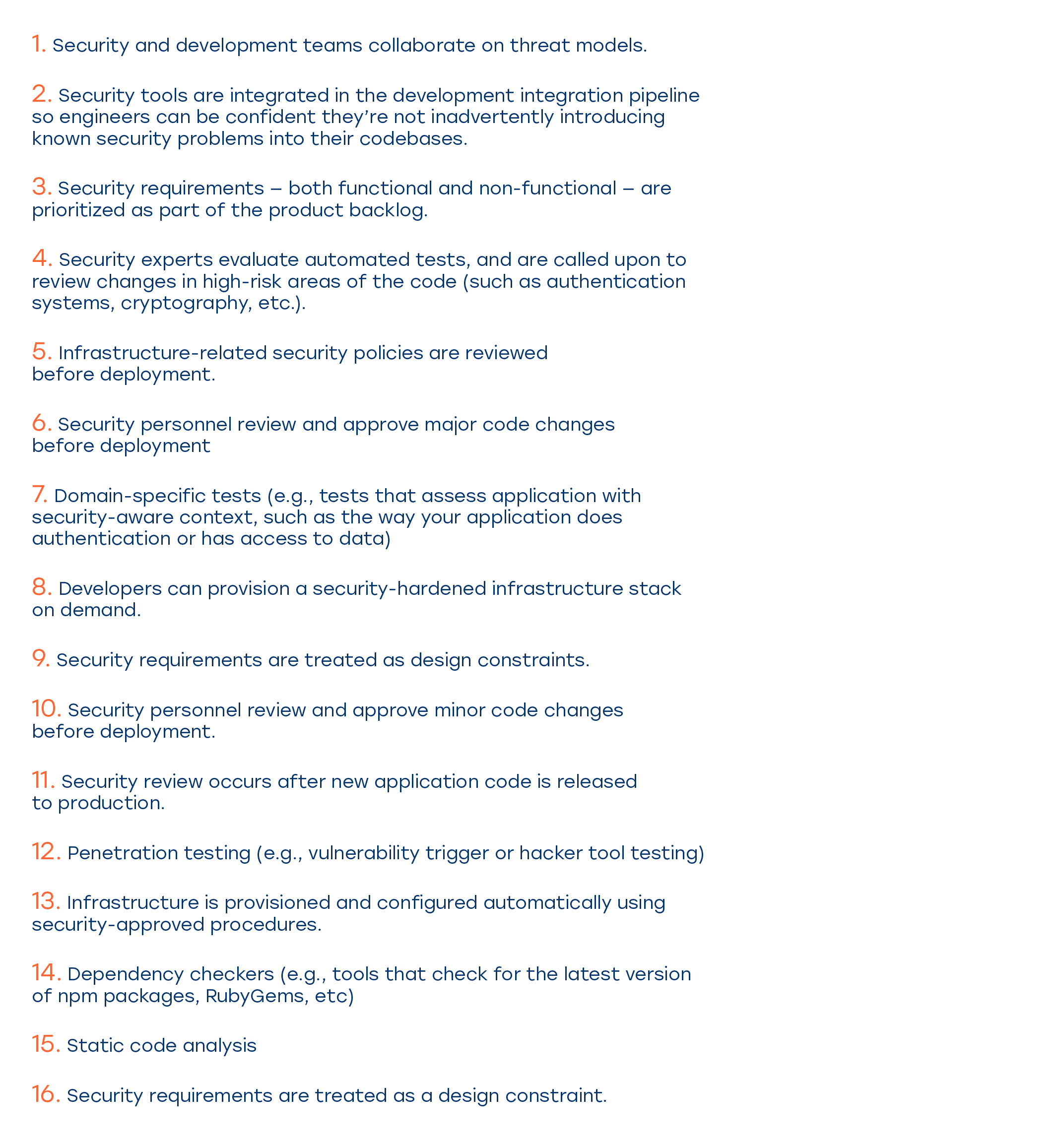
1. If you do the DevOps right, your cybersecurity implementation will also go well.
The reason for this situation is that DevOps culture encourages collaboration and communication between teams. DevOps empowers sharing the knowledge on the tools and skills, so the Devs and QA better know how to build their apps to be able to implement the security measures earlier on, while the Ops know how to organize the workflows to run the necessary security tests automatically.
When your entire IT department becomes a cohesive team working on a single goal, instead of throwing the responsibility across the wall to another division, your workflows become much more streamlined, predictable and productive. This simplifies the implementation of security procedures greatly, and 22% of top-performing companies that use DevOps practices have also reported success with their cybersecurity implementation endeavors.
2. Shifting the security procedures to the left and using automated security testing makes your teams twice as confident is their cybersecurity standing.
Let’s face it, most of the security testing has always been done just before the release and hotfixes have been bolted sideways to the new code batches directly before pushing new features into production. This has often resulted in post-release crashes and has cost a lot of nerves to all the members of the software delivery team.
Quite the contrary, when the security requirements are codified in form of automated tests and new code can be checked against them constantly throughout the development process, major post-release crashes and security breaches become literally nonexistent, which saves a lot of time and effort for your business. Puppet report highlights that the confidence in their cybersecurity measures grew 200% in the businesses that have successfully implemented DevOps workflows.
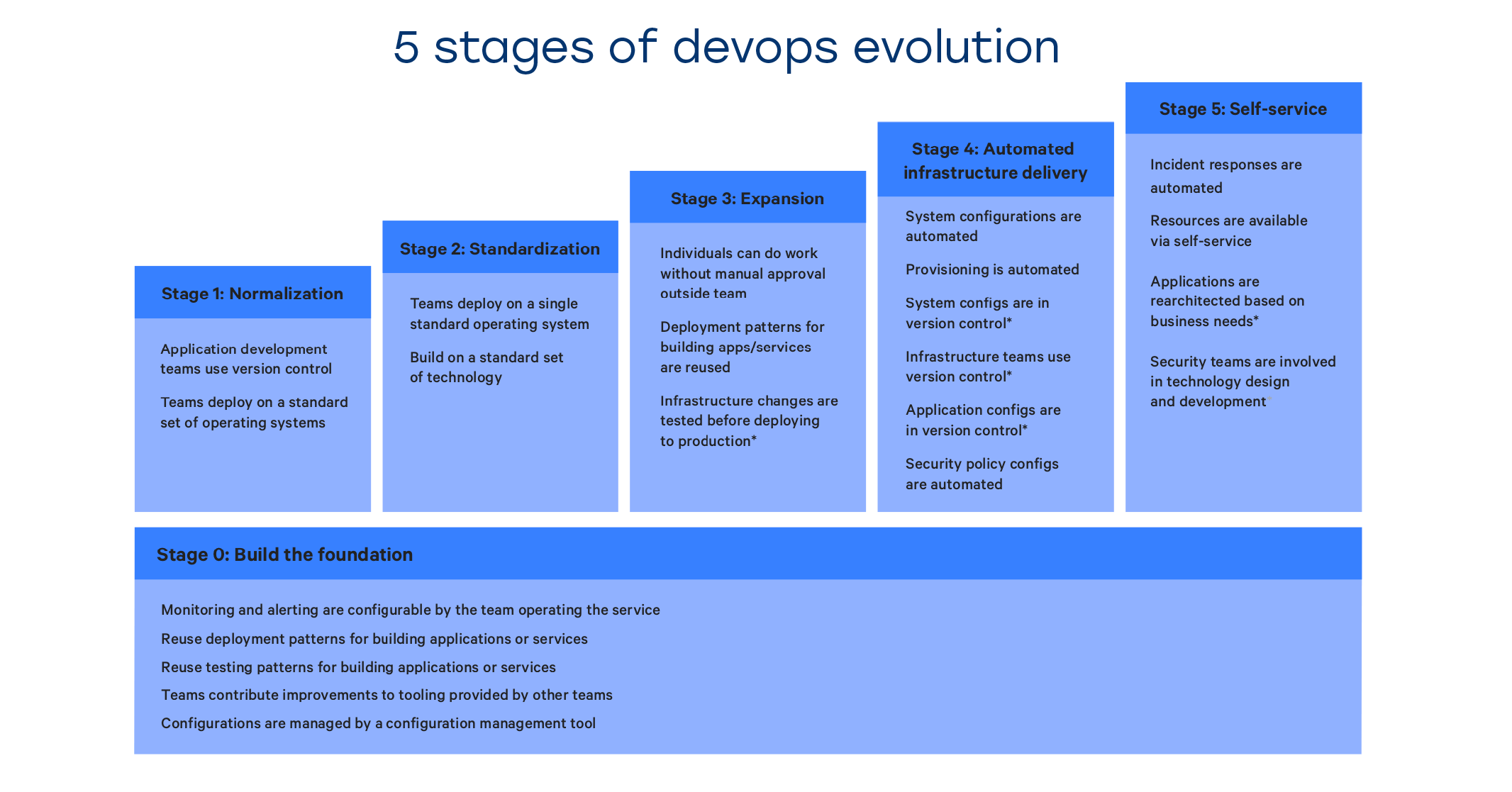
Here are the top 5 factors that contribute to improved cybersecurity standing:
- Developers and security engineers collaborate to define the possible threat models
- Security procedures are codified in the form of tests, so the developers can ensure they don’t introduce known vulnerabilities in their new code
- Both functional and non-functional security requirements are given top priority in the product backlog
- Security engineers perform an in-depth review of high-risk product areas (encryption, authentication, etc) before pushing the code to the staging environment, not before pushing it to the production environment for release.
- Security requirements are paramount when designing and implementing new infrastructure (Kubernetes Pod Security Policies, limited-time certificates and certificate rotation, LimitRanges and Resource Quotas, etc)
Thus said, thorough implementation of security procedures and practices helps save tons of time, effort and resources in the long run.
3. Cybersecurity integration provides immense benefits throughout the whole software delivery pipeline.
When cybersecurity demands become normal project requirements instead of dreaded scarecrows of periodic audits, the business benefits as a whole:
- Companies with the highest level of DevOps and security integration can deploy 2-3 times more frequently as compared to the medium-range or 10 times faster than low-performers. 61% of respondents to the Puppet survey stated they have fully integrated cybersecurity in their DevOps procedures and can deploy new code once a day or even faster.
- Time-to-recovery after incidents reduces significantly, though these issues are not completely excluded from normal workflows
- When security checks are tightly integrated with automated software delivery pipelines, companies can stop their push of the new code to release quite simply at any point to issue any updates necessary
4. Security integration does not come easy, especially in the middle stages.
It is easy to implement the basic cybersecurity requirements and address the most pressing demands. However, once the basics have been covered, it becomes unclear what to do next. Many businesses stumble from a roadblock to a roadblock and whilst they do overcome these challenges eventually, it is quite hard to reach operational excellence.
However, striving to achieve it is a good constant effort that helps keep your team motivated. The key here is not to lose faith, build a clear and transparent roadmap and solve the challenges as they arise — and one day you will wake up to see your cloud infrastructure a powerful, lean, mean and efficient machine! There are three important points to keep in mind in order to succeed on this stage of cybersecurity implementation:
- The flexibility of collaboration is paramount. Remove all and any roadblocks that might hinder your security measures implementation. Project goals must be aligned, tool kits must be shared, manual approval requirements must be removed. Managers hate revoking their approval (or denial) rights, but this is a crucial requirement for moving forward.
- Sharing and collaboration between teams. It is not enough to collaborate between the teams within the IT department. Your whole business uses IT tools and its general productivity depends on using them cost-efficiently. This means that IT department gets a say in many company-wide decisions, especially the ones involving technology. They are the ones who will run it and integrate it with the rest of the tools, so they must be the ones to choose it.
- From solving local pains to building long-term security strategy. The initial results of DevOps and cybersecurity implementation will cover the local pains — automating the software delivery pipelines and cloud infrastructure management, for example. However, once it is done, the security measures must be revamped and introduced to the business as a whole, forming a long-term security strategy that covers all aspects of operations to minimize the risk of malicious intrusion or system failure.
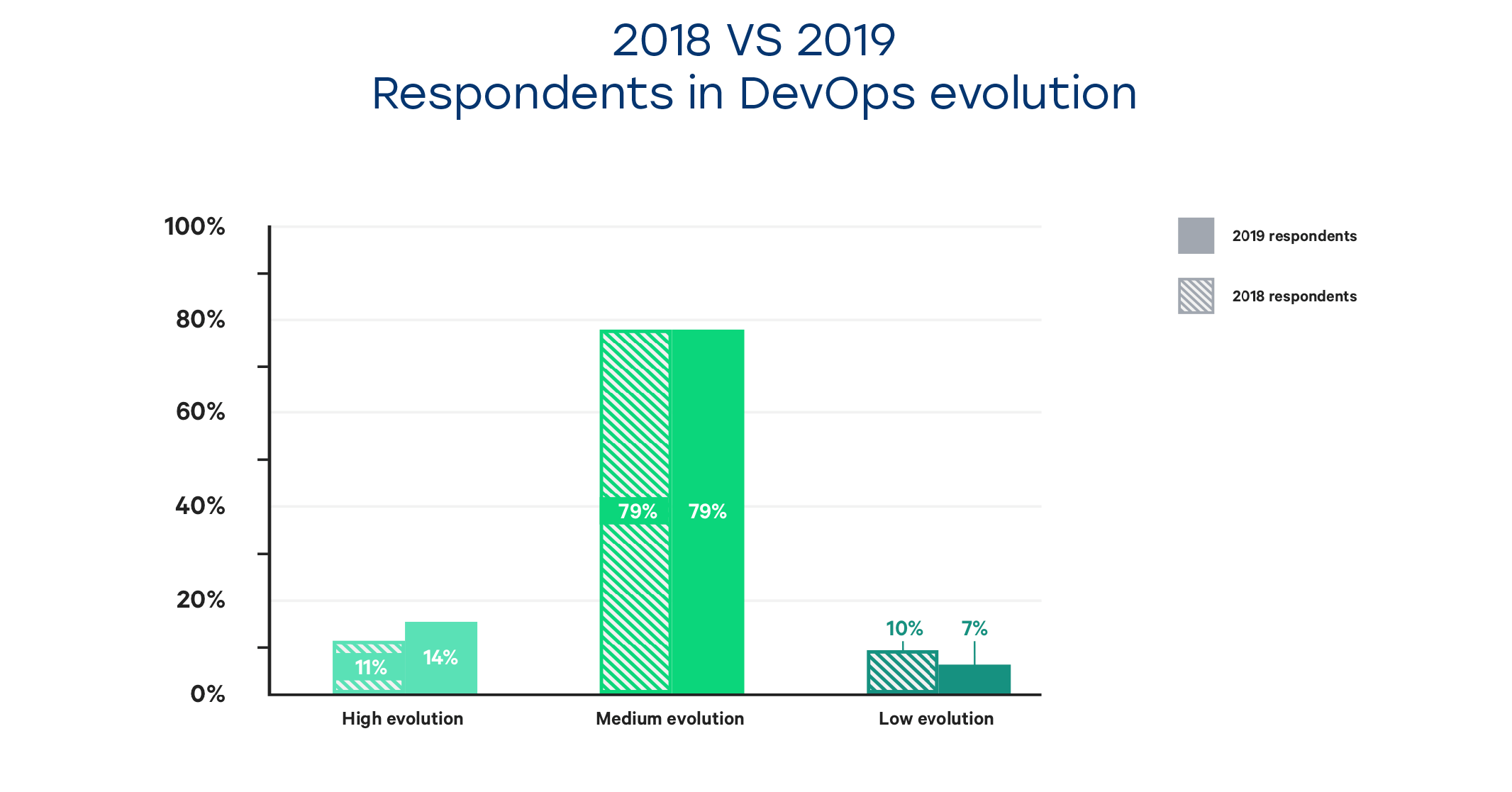
As you can see. most of the companies currently undergoing the DevOps evolution are now in the middle of their journey. However, as many of these reach the later stages at the moment, the percentage of high performers will steadily grow each year, as more and more companies will have their DevOps workflows implemented and security integration complete.
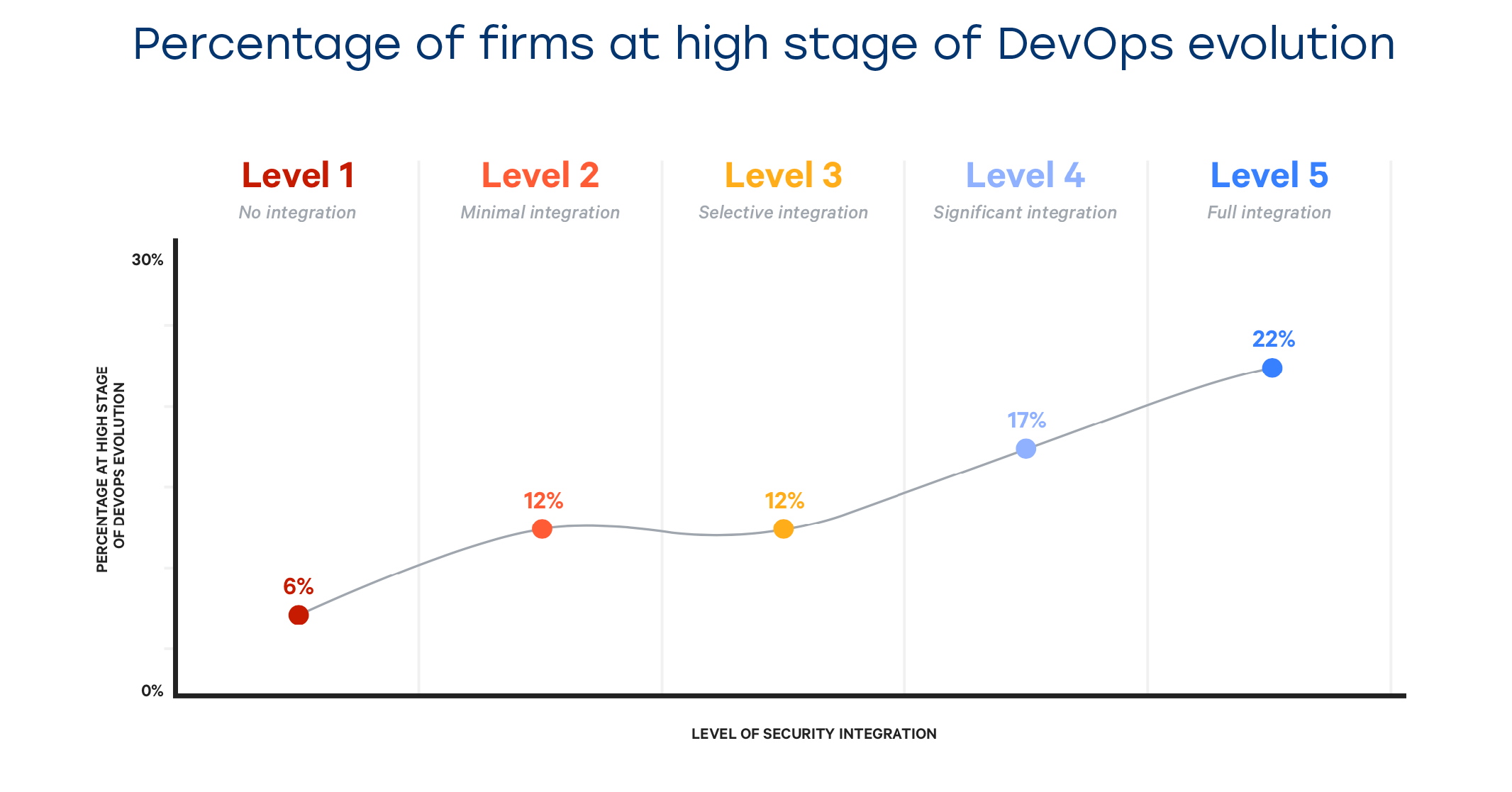
As you can see, most of the top performers (22%) have their security procedures fully integrated with their DevOps pipelines. This means that the whole cycle of security measures (vulnerability detection and correction, automated security policy audits and responses to their results) is applied on all 5 stages of the software delivery pipeline:
- Defining project requirements
- Product or feature design
- Writing the code and building it
- Testing new code via canary builds
- Deployment of new features to production and ongoing monitoring
Automating the security policy implementation throughout the majority of these phases significantly reduces the risk of unauthorized database access or suffering from a malicious intrusion — as the service exposure area is minimal, all channels of access are closed or controlled and the update/backup processes are watertight and resilient. Thus said, the gradation is as follows:
- No integration — no security checks on any of these stages
- Minimal — security involves 1-2 stages (usually in production and staging)
- Selective — security involves 2-3 stages (usually in production, staging and testing)
- Significant — security involves 3-4 stages (usually involving the code building stage)
- Full integration — security covers all 5 stages (security requirements are included in the design of any new product, service or feature)
Unbelievable as it might seem, 6% of highly-performing industry-leading businesses manage to operate without any cybersecurity checks and procedures in place. They handle the results of periodic security audits and seem to be getting away with just that — so security integration is not mandatory for your business.
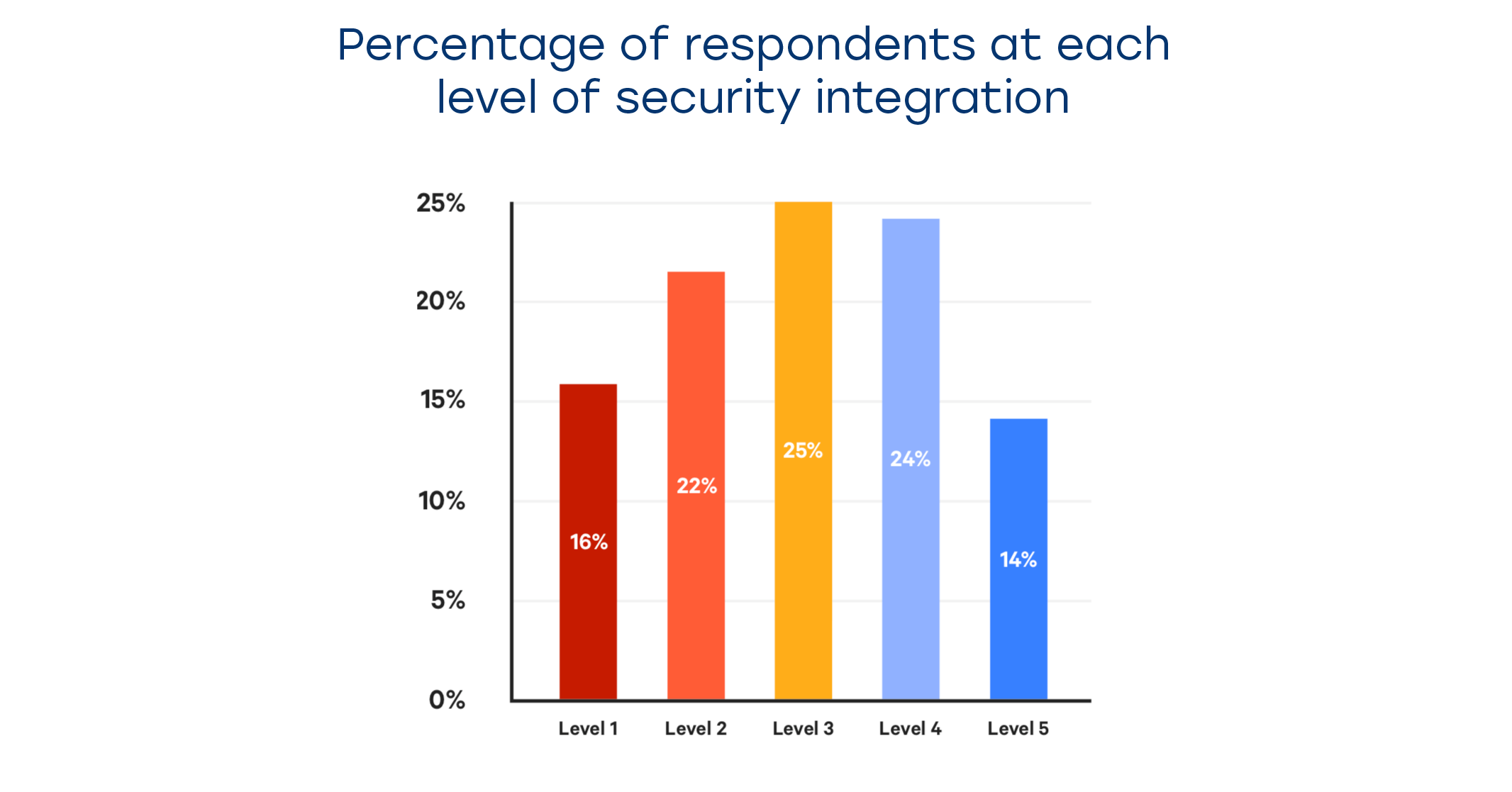
Thus said, the majority of survey respondents still had at least some security procedures in place, but only 14% were fully integrated, the rest currently being at the medium stages of their journey. The Puppet team has identified the key practices that contribute to successful security integration with all your business workflows across the entire company.
The top five points of this list relate mostly to the infrastructure management and software delivery processes — exactly what IT Svit escells at. Throughout 2019 IT Svit team has handled lots of DevOps projects and helped multiple companies implement their cybersecurity strategy to ensure their business objectives can be reached without major security threats. Below we showcase our approach to cybersecurity management.

IT Svit approach to cybersecurity implementation
IT Svit has acquired profound expertise with building cloud infrastructures, automating CI/CD pipelines and integrating cybersecurity features for our customers. One of the major insights of this year for us was the decision to begin building immersive cloud infrastructures using cloud-native services and components from AWS and Google Cloud Platform.
While we still can design and implement the cloud infrastructure for any project using open-source alternatives only, we are now firmly convinced that giving vendor-specific cloud web services a shot is not bad. After all, why limit yourself by not using the latest Amazon web services, if there are no reliable open-source alternatives yet — or they don’t provide the same level of integration? The question of price remain, but we can select the best fit for every situation to ensure your system is cost-efficient and performs well under heavy workloads:
- We build AWS and GCP infrastructure correctly — 1 environment per account, all logs are stored within 1 account
- We can use Amazon web services like Amazon Load Balancer to replace Ingress Nginx controller
- Amazon CloudWatch is a worthy alternative to Prometheus & Grafana
- Amazon CloudWatch Logs can be used well instead of the ELK stack
We have also adopted several important cybersecurity practices for our DevOps workflows:
- Kubernetes Pod Security Policies are enabled for all our projects
- Helm is used for all deployments and we configure it to meet your unique project requirements and manage all applications with ease
- Helm charts provide visibility through all the cluster components
- Cluster components authenticate each other using certificates
- These certificates are rotated under some clear policy and NEVER issued for 100 years. They serve their purpose as intended, not just to tick the box.
- Logs are audited, parsed and smart alerts are raised if needed
- Every cluster has a transparent and functional component update mechanism that can be used as often as needed without any issues and errors
- All service ports for the clusters are protected by the firewall
- Network policies enabled and configured
- RBAC authorization with strict control and understanding of RBAC roles
- External user authentication to access the cluster is done using a centralized user storage like LDAP using some OAuth tool like Dex
- Kubernetes LimitRanges and ResourceQuotas are enabled and correctly configured for all namespaces
- Separate clusters for Dev/Stage and Production environments
- Any new abstraction can be launched only using the CI tool, and each CI project has granular control of specific rights and namespaces.
Thus said, there is a list of cybersecurity checks and procedures we can implement and manage for our customers:
- Penetration testing using KALI Linux
- Split-horizon DNS implementation for AWS and GCP
- Server- and client-side network isolation encryption
- RBAC and Multi-factor authentication implementation for all systems
- Password policies implementation, credential retention and rotation
- Smart monitoring, analyzing, alerting enabling intrusion early detection and automated prevention
- Building systems that operate with minimal human intervention, with automated workflows and restricted access to mission-critical business systems
- Network and process isolation with encryption for all data storage and connections
- SQL-injections to test your database integrity and remediate the potential breaches
- Cross-site scripting to check your data input form integrity and screening any user data input for malicious code
Thus said IT Svit follows the best practices of DevOps and cybersecurity implementation listed by Puppet, Splunk and SumoLogic and provides managed cloud computing services covering all the range of tasks your business might need to perform. We can help your business become a top performer and leverage all the benefits of the cloud. If this is something you need — contact us with your project requirements and we will make it happen!