Cloud Security: principles, hot topics, reliable platforms
-
5217
-
6
-
0
-
0
Cloud computing security becomes ever more important in a globalized world. This article covers 14 main cloud security principles, security-related topics and platforms.
Cloud computing security, or simply cloud security, is a set of tools, principles, controls and policies used to protect IP, financial data, customer details and other valuable information stored in the cloud, as well as the cloud infrastructure it resides on. Thus, understanding all the aspects of cloud security is important to ensure your IT operations in the cloud are on the safe side. Today we discuss cloud security principles as outlined by CESG, their implementation in AWS and Google, other topics related to cloud security like possible controls and defensive measures, and wrap up with a list of several proprietary and open-source cloud security platforms.
Cloud computing is not very secure by design, as virtualization of cloud computing resources creates a common layer for many hardware units. This layer must be protected from malware infestation or insider attacks, as any threat affecting one part of the system can propagate to all other system parts, affecting multiple users. This is why cloud service providers implement rigorous background checks of their personnel and strict security procedures for their facilities.
However, security is a double-edged sword and there is always so much a cloud provider can do. Cloud computing customers should also do their part, adhere to cloud security best practices and follow its basic principles. There are 14 main cloud security principles, formulated by the UK government’s National Technical Authority for Information Assurance (CESG). These were intended to be used by the UK cloud hosting companies, but as they turned out to be well-thought-through and the UK business makes a huge portion of the global market, these 14 principles of security in the cloud were adopted by AWS and Google and integrated with their internal security guidance procedures.
14 Cloud Security principles
Formulated in March 2014, these 14 principles of cloud security from NCSC depict all aspects of handling sensitive information in the cloud. However, not all of them are compulsory, so cloud customers must make their judgment calls regarding the applicability of these principles in their projects, the importance of each requirement and the degree of assurance they need regarding the applicability of these principles. On the other hand, cloud service providers must build their public cloud offerings around these principles to let their customers make informed decisions regarding their sensitive data storage and processing in the cloud.
- Protecting the data in transit
Customer data should be protected with network protection tools and encryption while in transit between networks. Otherwise, there is a risk of tampering with the data or eavesdropping on it by third parties with malicious intent.
- Protecting the data in storage
Customer data and the physical assets storing it must be protected from physical damage, loss, seizure or tampering. Not following this principle might lead to leaks of customer data, which will lead to legal sanctions from regulators and reputational damage to the cloud provider.
- Separation of customer data
Data and services of all customers must be separated from each other logically and through cloud functionality. Not following this principle would result in one compromised or infected user account being able to affect the sensitive data from the rest of the accounts.
- Governance framework
The cloud service provider should instate a framework governing all interactions with customer data and services to ensure their security. Not implementing this principle means any declarative, preventive, procedural or physical personnel security controls will not be effective in dealing with potential security breaches. In short, it is not enough to have the tools in place — the staff must know how to use them and what tools to use in every situation.
- Operational security
Cloud service providers must ensure the operational security of their daily routine by implementing the procedures and processes for monitoring the system performance. If this is not done, the cloud computing provider’s staff will not be able to ensure the security of their customer data during a malicious attack, not to mention detecting, impeding or preventing it.
- Staff security
Cloud hosting providers must perform rigorous staff security screening before the employment and provide periodic staff security training for their roles. If this principle is not followed, the chances of mishandling the sensitive data due to not-knowing or malicious intent are much higher.
- Security by design
Cloud computing services must be designed and built according to strict security requirements to be able to identify and resolve potential security threats. If this is not done, the services might be subject to security breaches and loopholes, potentially compromising the service functionality and the customer data within.
- Supply chain security
The cloud service platform must ensure all its contractors follow and implement the security practices the service provider claims to uphold. Failure to implement this might result in any person from the supply chain being able to undermine and compromise secure customer data within the service.
- Customer management security
Cloud service customers must be provided with the necessary tools to securely manage their data and operations in the cloud. If this principle is not followed, there is a risk of unauthorized access of one customer to other customers’ data.
- User authentication and authorization
Only properly authenticated and authorized users (both from the cloud provider’s and the customer’s side) must have access to cloud service interfaces. Failure to implement and exercise this principle leas to data theft and service modification with malicious intent.
- Protection of external interfaces
All cloud interfaces that come in contact with external systems (system APIs, data entry endpoints, etc.) are considered less secure and must be provided with additional layers of security, protection and monitoring. Not implementing this principle results in such interfaces increasing the potential attack surface and becoming access points into the system for the attackers.
- Service administration security
All workflows and routines used by the cloud provider’s administrators must be designed to ensure maximum security of data and service handling, and compliance with these routines must be periodically checked. If this requirement is not meant, an attacker that imposes itself as an admin might gain control over the system and get access to large volumes of sensitive data.
- Availability of security audit information
Cloud users must have the means to monitor the process of storing and processing their personal data and audit the security practices in place. If this principle is not implemented, the users will have no way of detecting the mishandling of their data within any reasonable timescale to instate effective recovery procedures.
- Customer is responsible for secure cloud use
Cloud computing users are responsible for securely storing their access details and using their cloud service in a secure way. If this principle is not followed, no security measures from the cloud provider’s side can ensure the safety of the service and data held within it.
As you can see, these principles are logical, cover all aspects of cloud security operations and can be implemented within a reasonably short time by the cloud providers. Ther 14th principle, however, is the most important one — as the cloud security can be very easily compromised by using a simple password or granting service access to unreliable people.
Applying cloud security principles in your daily operations
The 13th principle is also very important, as it highlights the way for cloud customers to actively exercise their rights and responsibilities — by regularly auditing who handles their data and how it is done, both in the cloud and within their own organization. This is actually one of the pillars of the GDPR implementation.
Your company can do this by adhering to three reliable guidelines:
- Working with a secure and trusted cloud service provider (AWS, Google Cloud, Azure)
- Following GDPR in your business or organization to constantly monitor who handles your sensitive business data and how it is done
- Ensuring your cloud infrastructure is fully integrated with any existing information architecture.
Working with secure cloud service providers
Once these 14 security principles from NCSC came out, all reputable cloud computing providers made it a point to showcase they implemented them and comply with these requirements. Namely, Amazon Web Services, Google Cloud and Microsoft Azure all have the ISO 27017 accreditation, meaning they comply with these NCSC principles.
There also is another indicator — how open is a cloud platform to third-party security audits. Google Cloud, Azure and AWS do it with ease. As a matter of fact, Google Cloud is named the most secure cloud platform by Gartner or Forrester almost annually, and Amazon has published a whitepaper on how AWS implemented 14 NCSC security principles. AWS makes an emphasis on building a shared responsibility environment, where the customers are responsible for securely configuring their applications and platforms, and AWS is responsible for securely configuring and running its global infrastructure.
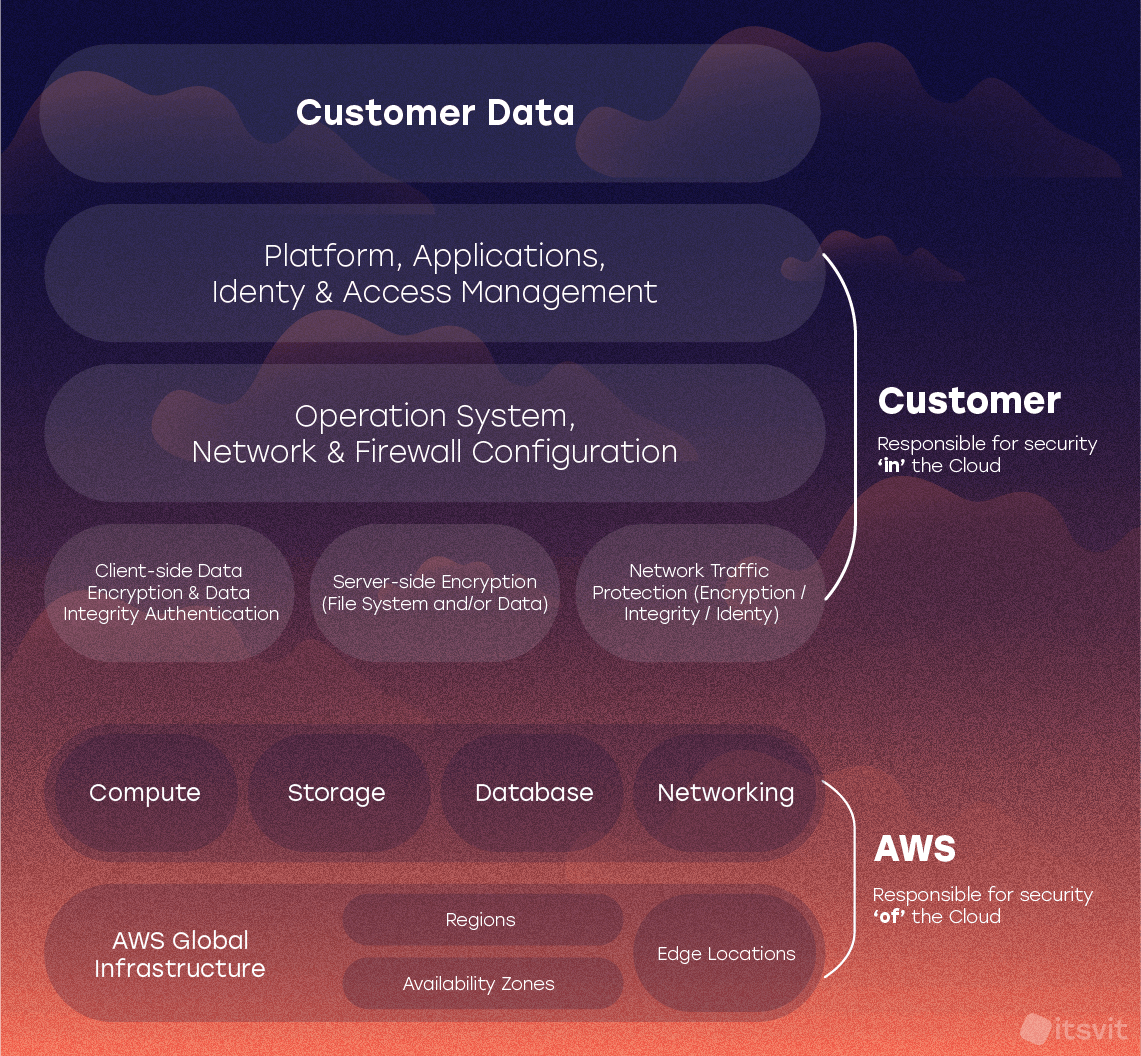
The whitepaper available through the link above showcases all AWS features and services used to implement and support the 14 NCSC principles.
GCP has also published a whitepaper on Google Cloud’s compliance with the UK’s cloud security principles. It explains in detail how Google builds its infrastructure and services to enable its customers to benefit from the implementation of these security principles. It is a thorough demonstration of Google’s systematic approach to cloud computing services delivery with multiple links to Google Cloud documentation.
Following GDPR in your business or organization
One of the implications of GDPR and NCSC cloud security principles is that the cloud service consumers must not passively trust their cloud computing providers with their data. Instead, you must actively exercise your rights and responsibilities within the GDPR scope. You must design a data protection framework within your organization and appoint a Data Protection Officer responsible for monitoring compliance with it.
On the other side, you must actively audit the process of your sensitive data storage and processing by your cloud service provider. By embedding security checks and compliance procedures in your daily workflows, you will keep your staff up-to-date and able to respond quickly to any cloud security issues should they arise.
Ensuring your cloud infrastructure is fully integrated with the cloud
This is essential for larger enterprises that face the need to move their data, applications, and processes into the cloud but have to overcome the limitations of existing legacy infrastructure. This means either moving vast volumes of data to private cloud storage or building hybrid cloud solutions, where some systems and operations work in the cloud, while sensitive data is securely stored on-prem.
However, this demands building complex authentication and authorization workflows for all the processes that interact with the cloud and on-prem systems. Ensuring the security of data during such transit and processing is actually one of the hottest cloud security topics nowadays when global corporations are forced to work remotely due to the COVID-19 outbreak and have to adapt their systems and workflows accordingly.
This requires following one of three approaches:
- Opting for cloud-specific security solutions like AWS CloudTrail, Azure Security Center or Google Security Command Center
- Buying proprietary cloud security platforms like Trend Micro Deep Security for hybrid cloud, Alert Logic Cloud Insight, Alien Vault USM from AT&T, or ForcePoint Web Security
- Working with Managed Services Providers to build custom security monitoring systems using open-source tools and cloud-specific components.
Let’s take a closer look at the pros and cons of all of these approaches.
Cloud security platforms and custom solutions
The first option is to use the security measures developed and enabled by your cloud service provider. These solutions have the obvious benefit of being customized to work best with the rest of the corresponding platform’s products and services. Such solutions provide a combination of security controls that fall into 4 main categories:
- Deterrent controls — like warning signs around private property, such controls are in place to warn potential attackers of imminent retaliation. While nobody expects them to stop the wrongdoer, they do reduce the potential attack surface and act as an early warning system about the starting attack.
- Preventive controls — features like 2-factor authentication and strong passwords, that reduce the chance for a fraudster to impersonate a legitimate cloud user.
- Detective controls — procedures, scripts and features that actively detect and respond to threats. In case the attack takes place, such controls enact preventive or corrective measures to stop the attack or mitigate its consequences. All cloud security platforms that monitor the networking and performance of your cloud systems fall under this category.
- Corrective controls — features and scripts that reduce or remove the damage done by the attack. An automated reboot of a compromised Docker container or automatic loading of a backup file to restore the system after failure are examples of corrective controls.
For example, AWS CloudTrail provides ample statistics and information on who accessed your AWS account, from which IP, and what was done in the system. The same goes for GCP and Azure alternatives — all of them provide granular control over operations and interactions within their respective platforms.
The downside, however, is the increased complexity of configuration when using third-party software and hybrid systems, as it will require providing custom connectors and APIs. In addition, using cloud security features contradicts the idea of third-party audit and enterprise-grade businesses cannot risk losing billions of dollars worth of information due to using a tool that was not able to detect an insider attack. The last, yet not the least important factor is that going full throttle on using some cloud services means vendor lock-in — but the cost of the transition project is usually so high that it makes the choice final anyways.
Cloud security and monitoring solutions
Thus said, there is a variety of custom-built and highly-configurable cloud security platforms for enterprise businesses that allow avoiding these limitations and provide expert security monitoring of both your and cloud system parts in hybrid infrastructures. They are listed below, in no particular order.
Trend Micro Deep Security for hybrid cloud — an anti-malware and file integrity solution for enterprise-grade VMware environments. Deep Security is arguably the best solution for virtual infrastructures and this Trend Micro product forms a centralized dashboard for controlling all aspects of network interactions on your user machines and servers. The software agents run on additional VMs without disrupting the operations of your main infrastructure, and centralized alerting enables the admins to identify and resolve threats like malware quickly. Unfortunately, the price is quite high and regular updates require constant reconfiguration of the system.
Alert Logic Cloud Insight — an AWS-native cloud security solution that constantly scans your AWS infrastructure for vulnerabilities and misconfigurations. Using this tool admins can configure granular control for various users and have in-depth monitoring of all user activity within your ecosystem. When integrated with Amazon GuardDuty, Alert Logic instantly informs the users of active threats, issues recommendations on applying GuardDuty findings and helps ensure no similar attacks occur in the future by closing the security breaches.
Alien Vault USM from AT&T — A solution for centralizing all the login procedures in one secure cloud and filtering the traffic within your private cloud infrastructure. It is very cost-effective for mid-to-large enterprises with geographically disperse workforce and allows triggering an alarm (ad response) on any suspicious activity at once. From asset discovery to file integrity checks, monitoring of mission-critical assets and SIEM ready to go after installing, Alien Vault USM is a solid solution for organizations that value their security.
ForcePoint Web Security — this is a great solution for detecting possible insider attacks in global corporations. It filters the traffic and blocks or locks out the websites you consider malicious, or the ones that are not necessary to visit during work hours. Due to the centralized access management center and in-depth SSL filter, ForcePoint helps monitor and control traffic usage patterns to increase productivity and decrease risks across large enterprise organizations.
However, none of these solutions are perfect as none are built specifically for your business, and cannot be reconfigured to meet your needs in full, not to mention their subscription fees can be quite high. Thus said, many small-to-medium companies prefer working with custom-built systems that meet their specific requirements.
Unique cloud security solutions for your business
Managed Services Providers like IT Svit specialize in enabling cloud security, monitoring, smart alerting and automated response scenarios for your cloud systems. Built using cloud platform-specific and open-source components, such systems are cost-effective, flexible and can be configured to meet all your business requirements. In addition, due to our in-depth DevOps expertise with AWS and Google Cloud services, IT Svit team can build systems using cloud features to their full extent without actually ending up in vendor lock-in.
Thus said, every business that takes its long-term success seriously must think about ensuring its cloud safety, compliance and operational resilience. Following the 14 basic cloud security principles, working diligently on enforcing and following your security governance framework, using platform-specific or bespoke cloud security tools — all of these are necessary components of ensuring watertight operational performance for your business.
This becomes especially important in the outbreak of COVID-19, as the world faces the need to go online more and conduct work remotely. Establishing correct cloud security procedures can become essential for ensuring your survival and success — and IT Svit would be glad to help you with it!